
CyberDik Internet Security Services
Cyber Security, Forensics and Cloud Investigations
Cyber Security Intelligence
Exploiting cyber criminals helping you protect your personal and business information
Cyber Security poses a significant challenge to businesses and people; many do not understand the security implications of Big Tech's online computing machine. Several vulnerabilities have been exacerbated by the rapid and forced digitization of your data combined with the increased reliance of online data.
CyberDik was created to diminish and hopefully eliminate shady cyber activity before a cyber attack can happen.
Network Block Lists and Device Stalker Security
Unfortunately, privacy and protection is your responsibility today. Protection agencies, like the UK, US governments helped to create the evasive big tech enterprises through anti-trust lawsuits, manipulating laws, and to the eventual forcing of companies to the big tech servers in the "CLOUD". Even the personal computer operating systems have been corrupted.
While these countries and businesses claim to be taking steps to improve cyber resilience, big tech and the social online media corporations are consistently finding new ways of evading legal issues to evasively collect more data from you.
If you on a personal computer with Windows, server, workstation or desktop, open the File Explorer and make a mistake in the address bar. Your info just went to Bing.com a search engine. What if that info was related to a top secret project with intellectual property in the title?
CyberDik was created to bring awareness and to inform people of the issues with software, hardware and the foggy Internet called 'The Cloud'.
First Responder Cyber Security Tools
CyberDik Cyber Abuse Reporting
Report abusive IP Addresses here.
Report Abusive IP AddressARIN RDAP Lookup
ARIN API Lookup: https://rdap.arin.net/registry/ip/(ip address)
Report an abusive IP or Subnet to ARIN.
Report public fraud to arin.netICANN Lookup
Look up the current registration data for domain names and Internet number resources (IP Addresses).
The tool uses the Registration Data Access Protocol (RDAP) which was created as a replacement of the WHOIS (port 43) protocol.
ICANN RDAP Lookup
Cyber Dik Private Eye Cyber Services
We provide Network Penetration Testing, Business Platform Audits, Cyber Security Consulting and Professional IT Services to ensure that your business is accessible and secure.
Services We Provide
- Cyber Security Consulting
- Network Penetration Testing
- Business Platform Audits
- Secure Business Cloud Engineering
- Bare Metal Cloud Servers
Helping you Keep Your Business and Personal Information Secure
Illuminating Cyber Trolls across the WORLD
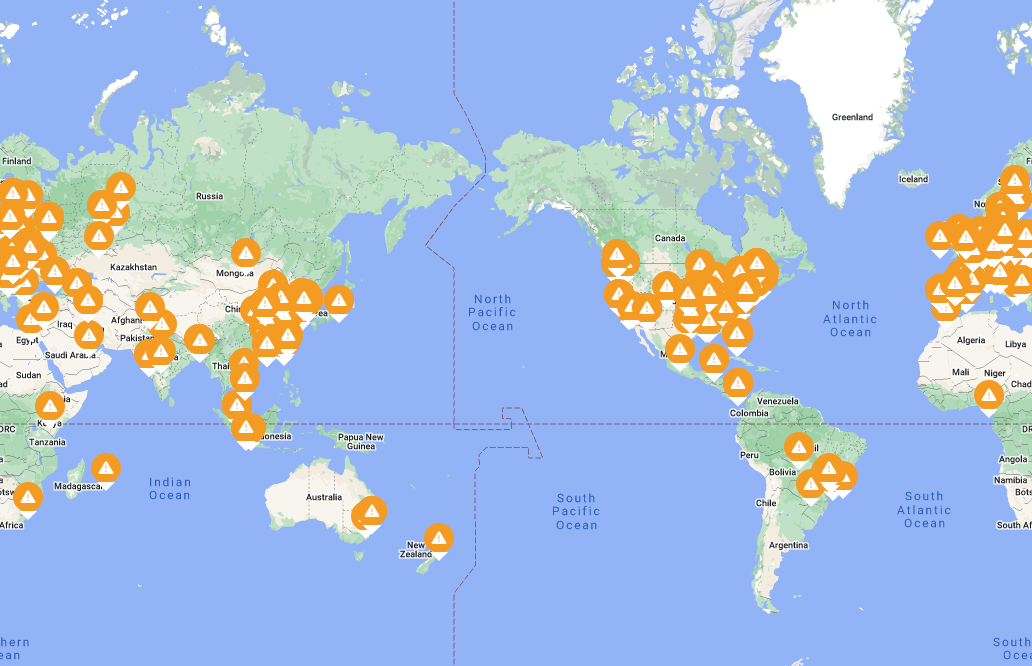
Cyber-Attack Monitoring
Our automated services monitor WWW, DNS, RDP and other web facing services trapping malicious criminals we call Trolls. Once a troll is discovered our troll hunting services tracks down their location, identifying data and alerts the responsible datacenter with the associated cyber attackers’ information. Our ambition is that the Datacenters take responsibility by blocking and removing the cyber attacker from their network and to notify local authorities.
Cappin' the Cyber Trolls at the Network.
The fastest and most effective way to get rid of Cyber Trolls is to cut them off at the network.
CyberTip: If you dont use IPv6, remove or disable IPV6, as it's a potential backdoor if not configured. It is an unecessary IP protocol and not necessary on standard networks. Many ISP operators do not use it.
We build several honey pot traps to capture thousands of network cyber trolls. We caught thousands of trolls attacking our honeypots revealing their information which we have visually mapped using Google maps.
CyberDik Block Lists
CyberDik API block lists are updated as soon as a troll is verified. Our Block Lists are categorized by service attack with links to hosts files, Cisco command line, and Windows PowerShell scripts.
The Price Of Free is your freedom of privacy.
Today, you have to block rouge services and even discontinue using certain technologies from your personal computers, smart "stalker"" devices and networks. Thanks to stalker companies like Taboola.com, OutBrain.com, Facebook.com and many other online social services along with hidden companies like, ShadowServer.org, Cloudflare.com, and countless others to the forced technologies like Microsoft, Google, and Apple.
Cloudflare.com is a DNS censorship service that is cleverly built into most browsers today via mDNS and also provides services for several search engines to block and shutdown websites. Many routers today have Cloudflare or similar services built in like the Arista Routers for example that our datacenter uses with Cloudflare DNS services imbedded in the firmware OS.
Microsoft’s evasive Bing.com services which is so deeply imbedded into all Microsoft Windows operation systems and is almost impossible to block with services and useless feature updates that consistently unblock windows firewall rules, yes, the Windows firewall is useless.
Worse yet is that “File Explorer” on your Windows personal computer can and will send your private data to Bing’s public search engine. Which is logging your IP address and other meta data along with your private file name and folder location. This is your private computer a PC.
The most recent stalker tactics today is the DNS switch using bs security manipulation pushing mDNS (appropriate acronym; manipulated DNS) on your browsers, bypassing your network security, which funnels your DNS requests to a company like Cloudflare.com or bing.com to monitor and potentially control what you are looking at.
The following Troll categories below can be used to block Internet Cloud Trolling Services from stalking your network, servers, computers and other online devices. Use these lists with a Firewall after your ISP to safeguard your network.
Legal Action in cyber security.
Here is an interesting company that is not in the spot light, CENTRIPETAL NETWORKS patents, what we find interesting is that they are suing firewall companies on cyber security patent law. These patents range from 2020-25 for packet rules, which is old news and public use, I don't understand how they got approved in the first place as cisco was already there. But what is really concerning is how they won a lawsuit against Cisco firewalls then lost recently on appeal. It clearly shows DOJ party biasness over the years from democrat to republican.
I wouldn't doubt that they are implicated in the cisco China chip swap fiasco that almost killed Cisco. Corporate democratic espionage? The crooked world we live in.